What to Look for in a SOCaaS Provider: Expert Selection Criteria
Security Operations Centers (SOCs) are foundational to modern cyber defense—yet not all SOCs operate at the same level of capability, efficiency or effectiveness. The SOC maturity model is a structured framework that helps organisations assess where their SOC stands today and, crucially, what capabilities it should develop next to keep pace with evolving threats, compliance expectations and business risk tolerance.
In this article, we explain what SOC maturity means, how maturity models are constructed, the characteristics of each maturity level and how this understanding informs strategic decision-making in risk management and security governance.
What Is a SOC Maturity Model?
A maturity model is a structured framework that describes the evolution of operational capabilities across people, process and technology. In the context of SOCs, maturity models provide a roadmap that illustrates how security operations evolve from basic, reactive activity to proactive, predictive and optimised operations.
At its core, the model enables organisations to:
-
Assess current capabilities and gaps
-
Benchmark performance against peers and standards
-
Prioritise investments in people, tools, workflows and automation
-
Align security operations with business risk appetite and compliance requirements
The concept of maturity models is widely used across disciplines (e.g., Capability Maturity Model for software) and emphasises continuous improvement rather than a static set of capabilities.
Why SOC Maturity Matters
A mature SOC is more than a team that field-strips alerts. Its strategic value lies in:
-
Reduced risk exposure through faster detection and effective response.
-
Operational discipline via repeatable, documented processes.
-
Compliance alignment with frameworks like SOC 2 and ISO 27001.
-
Scalable performance through automation and advanced analytics.
-
Business alignment where security decisions support organisational goals.
Without maturity, a SOC may remain largely reactive—responding to incidents only after they occur. A mature SOC aims to be proactive or even predictive, anticipating attacker tactics and reducing dwell time.
Typical Maturity Levels
While different models use slightly different terminology, most maturity frameworks describe a progression from rudimentary to highly advanced capabilities. A common structure includes five levels, often mapped to process, people and technology attributes.
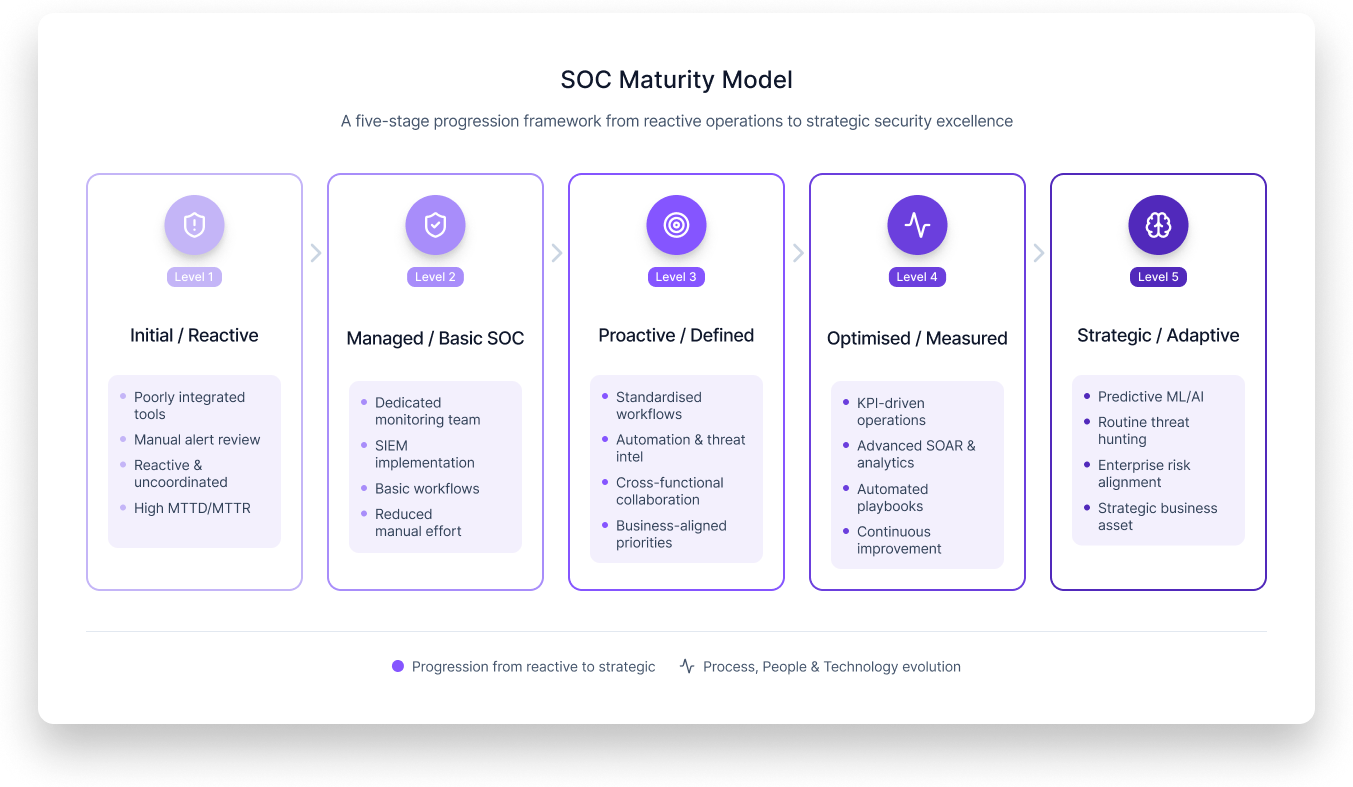
Level 1 – Initial / Reactive
At this stage, the SOC is nascent or ad hoc. Processes are informal or undocumented, and detection and response are largely manual and reactive.
Characteristics
-
Security tools exist but are poorly integrated.
-
Alerts are reviewed manually—with high false positives.
-
Incident response is largely reactive and uncoordinated.
Risk Profile
-
High vulnerability to new attack techniques.
-
Long mean time to detect (MTTD) and mean time to respond (MTTR).
This is the starting point for most organisations that have yet to standardise security operations.
Level 2 – Managed / Basic SOC
At this level, organisations begin to formalise their SOC. Basic processes are in place, and tools like SIEM (Security Information and Event Management) begin aggregating and correlating data.
Characteristics
-
Dedicated team responsible for monitoring and alerts.
-
Defined incident escalation and some documented workflows.
-
Basic threat intelligence integration.
Operational Focus
-
Establishing repeatable detection and response steps.
-
Reducing manual effort for routine alerts.
This level reflects an organisation that has moved beyond ad-hoc responses but has not yet fully automated or optimised operations.
Level 3 – Proactive / Defined
Here, the SOC evolves from simply reacting to threats toward proactively identifying patterns and integrating context into decision-making.
Characteristics
-
Standardised and documented workflows for detection, analysis and incident handling.
-
Greater use of automation and threat intelligence.
-
Cross-functional collaboration with other IT and risk teams.
Operational Advantages
-
Faster, more consistent response to incidents.
-
Better prioritisation of alerts based on business impact.
At this stage, the SOC begins to shift from tactical operations to strategic threat management.
Level 4 – Optimised / Measured
A mature SOC at this level combines advanced processes, tooling and governance. Monitoring becomes continuous and data-driven, and automation plays a central role in detection and remediation.
Characteristics
-
Metrics and KPIs guide SOC performance (MTTD, MTTR, false positive rates).
-
Advanced analytics, SOAR (Security Orchestration, Automation and Response), and threat hunting.
-
Incident response playbooks automated where appropriate.
Business Integration
-
SOC performance metrics are linked to organisational risk tolerance.
-
Continuous improvement loops inform tooling and process investment.
Achieving this level means the organisation is no longer just reacting; it is measuring and optimising security outcomes systematically.
Level 5 – Strategic / Adaptive
The highest tier of maturity represents a SOC that is fully integrated with organisational risk management and business strategy.
Characteristics
-
Predictive analytics and machine learning bolster detection.
-
Threat hunting and adversary simulation are routine.
-
SOC insights directly influence enterprise risk decisions.
Strategic Value
-
Alignment with enterprise risk and compliance frameworks.
-
Advanced automation reduces human effort for routine tasks.
-
SOC operations influence long-term technology and governance decisions.
At this stage, the SOC has become not just a defensive unit, but a strategic asset in enterprise resilience.
How SOC Maturity Aligns With Compliance and Risk Frameworks
SOC 2
SOC 2 reporting focuses on controls relevant to security, availability, confidentiality, processing integrity, and privacy. A mature SOC supports SOC 2 criteria by providing:
-
Documented processes and evidence of monitoring
-
Operational controls and incident response workflows
-
Alerts, logs and response records that help satisfy audit evidence
Progress through maturity levels typically correlates with stronger control evidence for SOC 2 assessments, as documented processes, automation, and consistent outcomes align with Trust Services Criteria.
ISO 27001
ISO 27001 requires a risk-based approach to information security and continuous improvement cycles through the ISMS. As a SOC matures:
-
Risk assessments are refined with better threat visibility.
-
Processes become standardised and auditable.
-
Performance metrics (e.g., MTTD/MTTR) inform risk treatment decisions.
A mature SOC supports ISO 27001 control objectives by enabling both preventive and detective controls that are monitored, measured and improved over time.
Using a Maturity Model to Drive SOC Strategy
A maturity model is not a rigid prescription; it’s a strategic tool. Organisations rarely leap from basic to advanced levels overnight. Instead, maturity evolves through purposeful investment in:
-
People – Analyst skills, roles and cross-functional communication
-
Process – Defined workflows, documentation and governance
-
Technology – Integrated tooling, automation and analytics
Roadmaps informed by maturity assessment help identify capability gaps, justify budget decisions, and prioritise initiatives with the highest impact on security outcomes.
Conclusion
Understanding the SOC maturity model equips security leaders with a structured view of both current capability and future progression. From reactive beginnings to strategic foresight, maturity models provide benchmarks and guidance that align security operations with enterprise risk management and compliance expectations.
Maturity is not a destination but a continuous journey that adapts with the threat landscape and organisational needs.
If you’d like, I can provide a self-assessment template or a roadmap example that illustrates how to progress through these SOC maturity stages in practice.
Dec 26, 2025 5:14:11 PM



