What Is SIEM and How Does It Work?
Introduction
For CIOs, CTOs, and CISOs, understanding the distinction between a Network Operations Center (NOC) and a Security Operations Center (SOC) is fundamental to effective IT management. While the NOC ensures your infrastructure runs efficiently, the SOC ensures your systems remain secure. Both play vital roles in maintaining business continuity but differ in purpose, tools, skill sets, and key performance metrics.
In today’s complex digital ecosystem, uptime and security are no longer separate goals—they’re interdependent pillars. This article explores the core differences between SOC and NOC, real-world examples of how organizations structure them, and the growing role of SOC-as-a-Service (SOCaaS) in achieving scalable, cost-effective security.
Purpose and Goals – Uptime vs Security
At their core, the NOC focuses on availability, while the SOC focuses on protection.
-
NOC’s Goal: Ensure systems and networks remain operational. Tasks include monitoring network performance, responding to outages, and ensuring service level agreements (SLAs) are met.
-
SOC’s Goal: Detect and mitigate cyber threats before they escalate. This includes monitoring for intrusions, malware, and insider threats.
The NOC combats non-malicious issues—hardware failures, latency spikes, or software misconfigurations. Meanwhile, the SOC fights malicious activity—phishing, ransomware, or data breaches.
Ultimately, both aim to support continuous business operations. The NOC ensures systems stay online, while the SOC ensures systems stay secure.
Teams and Skills – Network Engineers vs Security Analysts
The difference in mission drives a difference in personnel:
-
NOC Teams: Composed of network engineers, administrators, and IT operations specialists. Skills include network topology, bandwidth optimization, and device maintenance.
-
SOC Teams: Comprised of cybersecurity professionals such as analysts, threat hunters, and incident responders. Skills include log analysis, digital forensics, and malware investigation.
These roles are not interchangeable. A network engineer may excel at diagnosing performance bottlenecks but lack the forensic expertise needed for incident response. Conversely, a security analyst may detect breaches but not know how to reconfigure routers or troubleshoot a network outage.
Both teams require distinct yet complementary expertise—and together, they ensure resilience against both disruption and destruction.
Tools and Technologies – Monitoring vs Threat Detection Systems
NOC Toolset:
- Network Management Systems (e.g., SolarWinds, PRTG, Nagios)
- Application Performance Monitoring (APM) tools
- IT service management platforms (e.g., ServiceNow)
SOC Toolset:
- SIEM platforms (e.g., Splunk, IBM QRadar)
- EDR tools (e.g., CrowdStrike, SentinelOne)
- IDS/IPS, Threat Intelligence, and SOAR systems
Overlap: Both teams rely on logging, monitoring dashboards, and alerting systems. However, while the NOC uses these to ensure uptime, the SOC uses them to detect anomalies indicating compromise.
Metrics and KPIs – Measuring Performance and Protection
NOC Metrics:
- Network uptime percentage
- Mean Time to Repair (MTTR)
- SLA compliance and customer satisfaction
SOC Metrics:
- Mean Time to Detect (MTTD)
- Incident response time
- False positive rate and threat detection accuracy
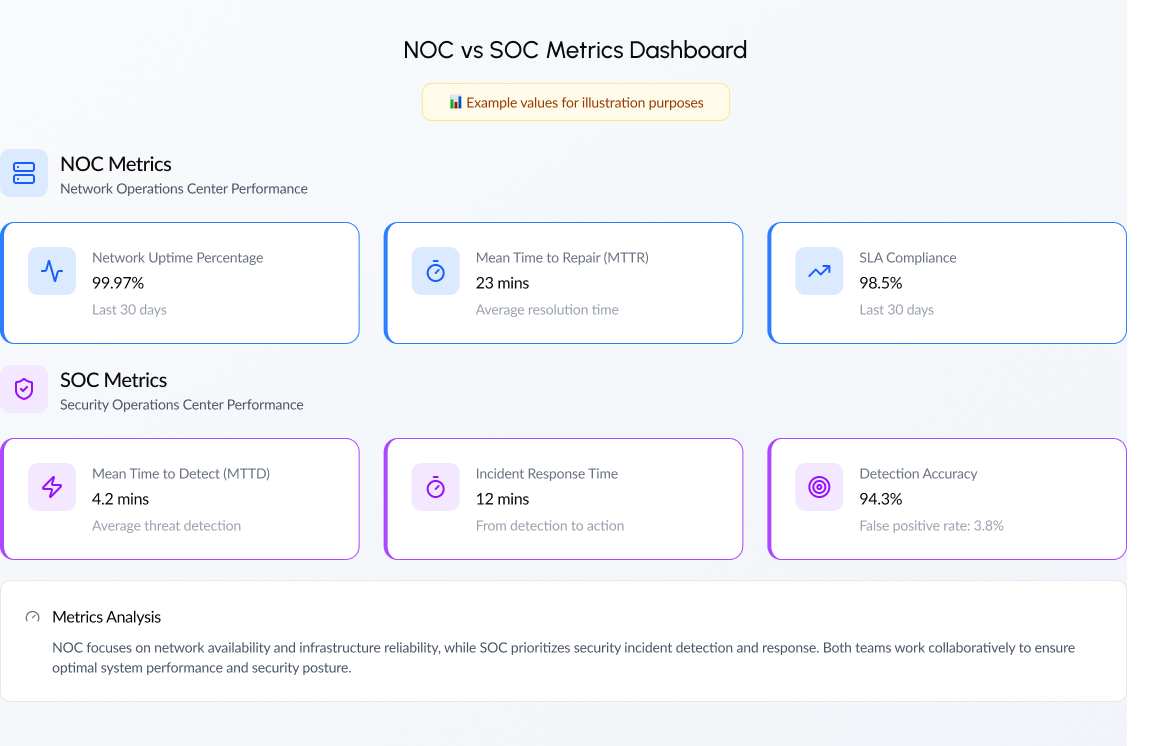
In short, NOCs measure reliability; SOCs measure resilience.
Separate vs Integrated Operations – Organizational Models
Organizations often debate whether to run SOC and NOC separately or in unison:
- Separate Model: Allows focus and specialization but risks communication gaps.
- Integrated Model (SNOC): Encourages collaboration and unified visibility, reducing incident response time.
Integration can be powerful but requires cultural and operational alignment—shared dashboards, processes, and cross-trained staff.
The Case for SOC-as-a-Service (SOCaaS)
Running an internal SOC is costly and resource-heavy. SOCaaS offers a scalable alternative by providing 24/7 monitoring, advanced tools, and expert analysts without the overhead of maintaining an in-house team.
Benefits include:
- Immediate access to expertise and technology
- Cost efficiency through subscription models
- Scalable services that grow with business needs
- 24/7 coverage ensuring continuous threat vigilance
Hybrid or co-managed SOC models let internal teams focus on strategy while external SOCaaS handles real-time monitoring and response.
For instance, Q-Sec’s SOCaaS integrates directly with client systems, acting as an extension of internal teams—combining external expertise with internal familiarity.
FAQs – SOC vs NOC Explained
-
Not effectively. While NOCs can detect anomalies, they lack the expertise and tools for deep threat analysis or response.
-
It depends on organizational maturity. Integration works best when teams share processes, tools, and training.
-
Aligning priorities—NOC values uptime; SOC values protection. Balancing both requires cultural shift and training.
-
SOCaaS offers proactive detection, response, and remediation—not just alert forwarding.
-
Absolutely. It allows SMBs to access enterprise-grade security operations at a fraction of the cost.
-
AI-driven automation, predictive analytics, and integrated SNOC models will define the next decade of IT operations.
Conclusion – Achieving Uptime and Security in Harmony
The NOC ensures systems stay operational; the SOC ensures they stay protected. Together, they form the backbone of modern digital resilience. Whether operating separately, in unison, or through SOC-as-a-Service, success lies in achieving balance—keeping networks up and threats out.
As organizations embrace hybrid and cloud environments, collaboration between SOC and NOC is no longer optional—it’s essential. The future belongs to those who can align uptime with security, achieving both performance and protection seamlessly.
Dec 22, 2025 5:38:59 PM


